CRITICAL (CVSS 10.0/10.0) Status: Active Exploitation Confirmed / Unpatched
Cisco has issued an urgent security advisory regarding a critical zero-day vulnerability affecting its email security and malware analysis appliances. The vulnerability has received the maximum possible severity score of 10.0, indicating it is remotely exploitable, requires no user interaction, and allows for total system compromise.
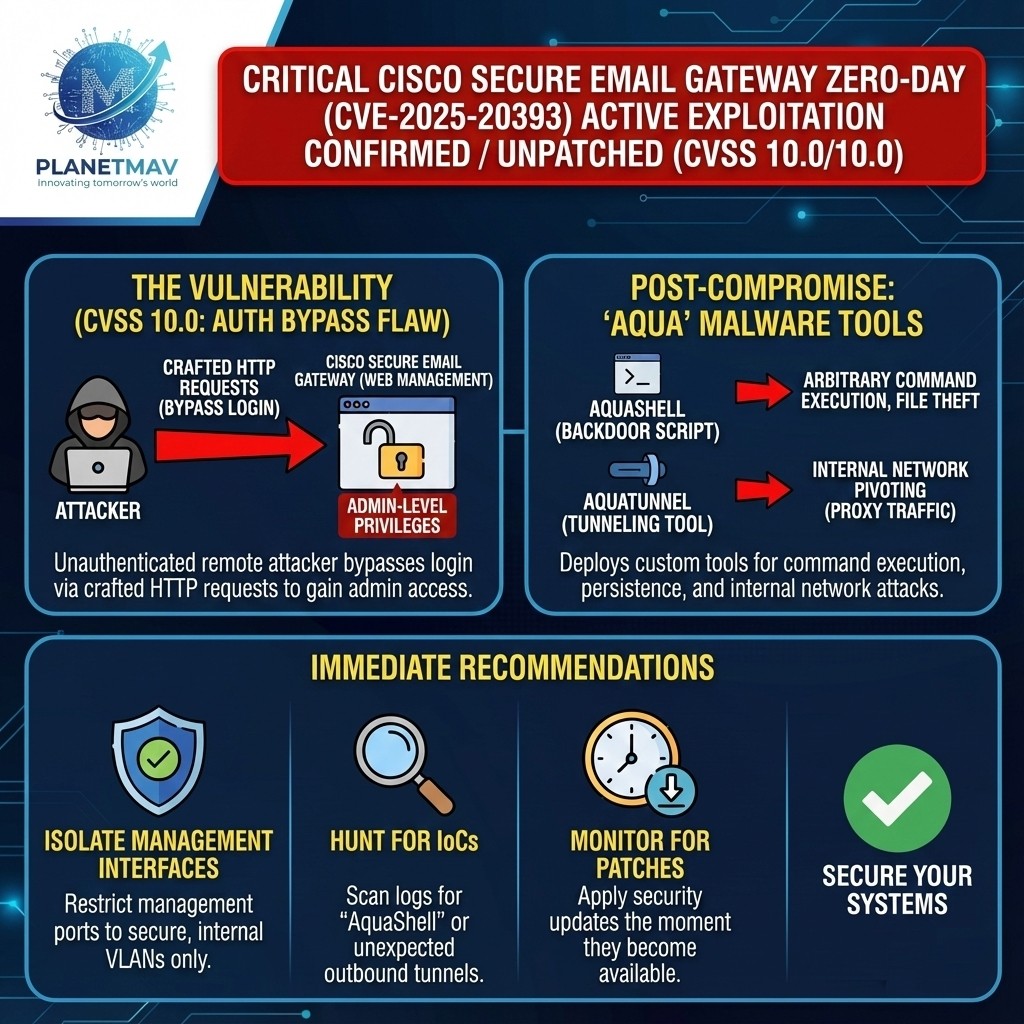
1. The Vulnerability Explained
The flaw, tracked as CVE-2025-20393, is an authentication bypass vulnerability located in the web-based management interface of the affected devices.
- The Mechanism: The vulnerability allows an unauthenticated, remote attacker to bypass the device’s login mechanisms completely. By sending specifically crafted HTTP requests to the management interface, the attacker can gain administrator-level privileges without needing a valid username or password.
- The Access: Once the authentication is bypassed, the attacker effectively owns the device. They can modify configurations, intercept email traffic, and access sensitive internal network data.
2. Post-Compromise: “Aqua” Malware Tools
Cisco Talos researchers have observed that threat actors are not just accessing the devices but are establishing long-term persistence using a sophisticated toolset dubbed the “Aqua” family.
Once the attacker gains admin access, they deploy the following:
- AquaShell: This is a custom backdoor script. It provides the attacker with a command-line interface (shell) to the compromised device, allowing them to execute arbitrary operating system commands, steal files, and manipulate processes.
- AquaTunnel: This is a tunneling tool designed to proxy traffic. Attackers use this to “pivot” into the victim’s internal network. Since the Email Gateway sits at the network edge, AquaTunnel turns the compromised device into a bridge, allowing the attacker to attack other internal servers while hiding their traffic inside legitimate encrypted connections.
- Persistence: The attackers modify system configuration scripts to ensure that both AquaShell and AquaTunnel restart automatically if the device is rebooted, ensuring they do not lose access.
3. Affected Products
The vulnerability affects the following Cisco appliances if remote management is enabled:
- Cisco Secure Email Gateway (SEG) – (formerly known as IronPort)
- Cisco Secure Malware Analytics – (formerly known as Threat Grid)
4. Immediate Recommendations
Because this is a CVSS 10.0 flaw being actively exploited:
- Isolate Management Interfaces: Ensure that the management ports (HTTP/HTTPS) of these appliances are not accessible from the public internet. They should be restricted to a secure, internal management VLAN only.
- Hunt for IoCs: Security teams should immediately scan logs for traffic related to “AquaShell” or unexpected outbound tunnels consistent with “AquaTunnel” behavior.
- Monitor for Patches: Cisco is working on fixes; administrators must apply the security update the moment it becomes available.

Comments are closed