CRITICAL (Hardware-Level Compromise) Status: Patches Available / Manual Action Required
A critical security flaw has been discovered in the UEFI firmware of motherboards from the world’s largest manufacturers. This vulnerability allows attackers to perform “early-boot DMA attacks,” effectively bypassing standard security protections like Secure Boot and antivirus software before the operating system even starts.
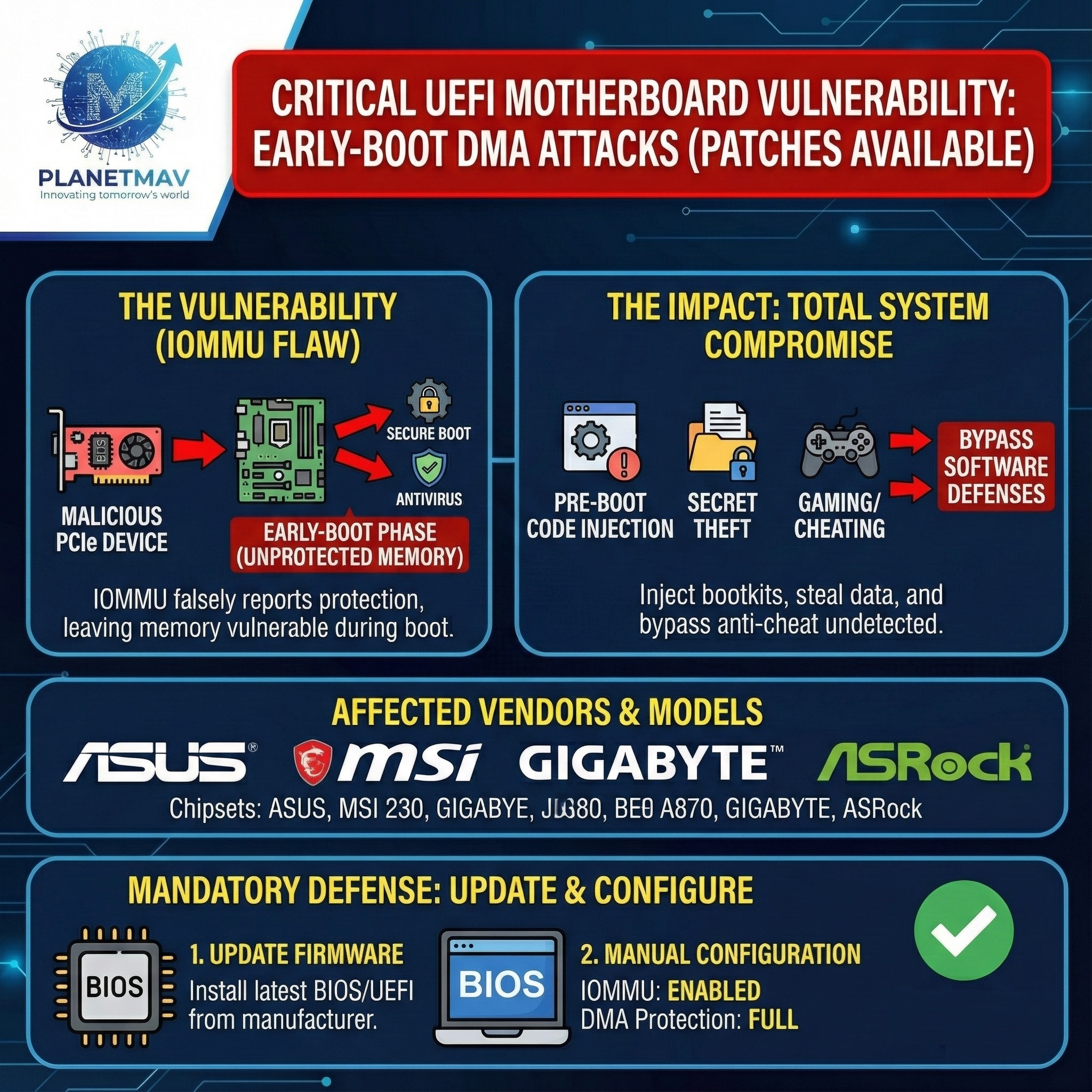
1. The Vulnerability Explained
The flaw lies in how the motherboard firmware handles IOMMU (Input-Output Memory Management Unit) protection during the boot process.
- The Flaw: Normally, the IOMMU is supposed to block unauthorized hardware from accessing system memory. However, on affected motherboards, the firmware falsely reports that DMA (Direct Memory Access) protection is enabled. In reality, the IOMMU is not fully configured or activated until the Operating System (Windows/Linux) takes over.
- The “Gap”: This creates a critical window of vulnerability during the “early boot” phase (the few seconds when the PC is turning on). During this time, the system memory is completely unprotected.
- Attack Vector: An attacker with physical access to the machine can plug in a malicious PCIe device (such as a specialized “DMA card” often used for video game cheating or research). This device can read and write directly to the computer’s RAM before the OS loads.
2. The Impact: Total System Compromise
Because this attack happens at the hardware level, it bypasses almost all software-based defenses.
- Pre-Boot Code Injection: Attackers can inject malicious code into the boot process, allowing them to install “bootkits” or rootkits that persist even after wiping the hard drive.
- Secret Theft: Attackers can read sensitive data (encryption keys, passwords) from memory before the OS can protect it.
- Gaming & Cheating: The vulnerability was notably highlighted by Riot Games, as it allows cheaters in games like Valorant to inject cheats that are invisible to anti-cheat software. Riot has begun blocking users with vulnerable BIOS versions from playing.
3. Affected Manufacturers & Models
The vulnerability affects a massive range of Intel and AMD-based motherboards from the top four vendors:
- ASUS: Intel Z490 through Z790, W790; and various AMD chipsets. (CVE-2025-11901).
- MSI: Intel 600 and 700 series chipsets. (CVE-2025-14303).
- GIGABYTE: Intel 600–800 series; AMD 600–800 and TRX50 series. (CVE-2025-14302).
- ASRock: Intel 500, 600, 700, and 800 series. (CVE-2025-14304).
4. Mandatory Defense: Update AND Configure
Simply updating your BIOS may not be enough. You must follow two steps:
- Update Firmware: Go to your motherboard manufacturer’s website and install the latest BIOS/UEFI firmware released this month (December 2025).
- Manual Configuration: After updating, enter the BIOS settings and manually ensure that “IOMMU” and “DMA Protection” (or “Kernel DMA Protection”) are set to “Enabled” or “Full Protection.” On some boards, the default setting remains insecure even after the update.

Comments are closed