HIGH (Active Massive DDoS Campaigns) Date of Discovery: December 18, 2025
A newly identified botnet malware family, officially dubbed “Udados,” has emerged as a significant threat to global infrastructure, specifically targeting the Technology and Telecommunications sectors. This botnet is orchestrating high-volume, sophisticated Distributed Denial-of-Service (DDoS) attacks designed to overwhelm networks with legitimate-looking traffic.
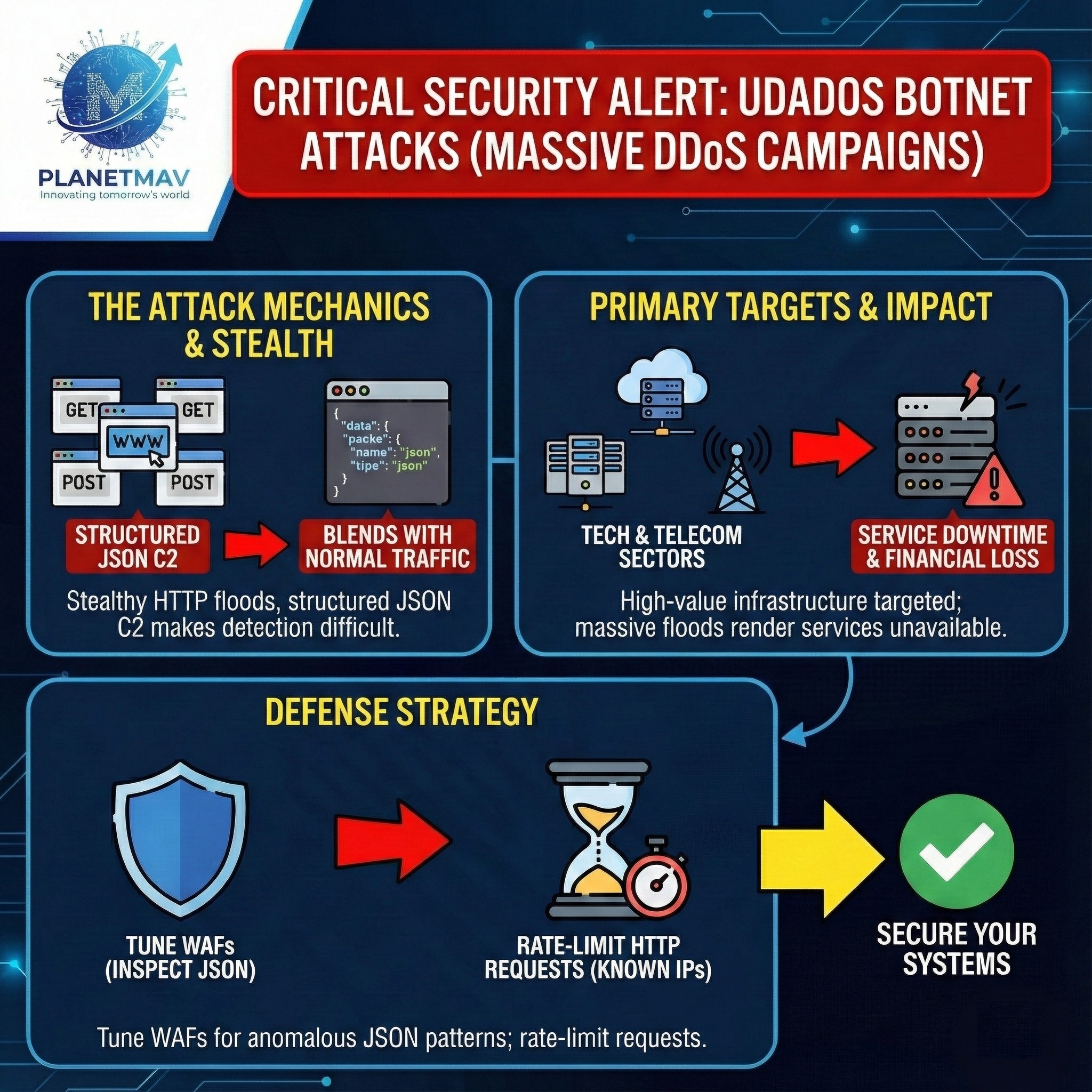
1. The Mechanics of the Attack
The Udados botnet distinguishes itself through a stealthy Command-and-Control (C2) mechanism that makes detection difficult for traditional security tools.
- HTTP Flood Tactics: The botnet primarily launches “HTTP flood” attacks. Unlike simpler attacks that blast random data, Udados instructs compromised devices to send high volumes of specific web requests (GET/POST) to the target’s servers, exhausting their resources and causing them to crash.
- Structured JSON C2: A unique feature of Udados is its communication method. Compromised hosts send structured JSON data to their Command-and-Control servers. Because JSON is a standard format used by millions of legitimate web applications and APIs, this malicious traffic blends in seamlessly with normal web traffic, effectively hiding the botnet’s activity from firewalls and intrusion detection systems.
2. Primary Targets
The campaign is currently focused on high-value infrastructure targets rather than random websites:
- Technology Sector: Targeting cloud providers, SaaS platforms, and data centers.
- Telecommunications: Targeting ISPs and backbone providers to disrupt connectivity on a larger scale.
3. Impact & Defense
- The Impact: The massive volume of the HTTP floods can render critical services unavailable, leading to significant downtime and financial loss for tech and telecom companies.
- Defense Strategy: Security teams in affected sectors should tune their Web Application Firewalls (WAFs) to inspect JSON payloads for anomalous patterns and rate-limit HTTP requests originating from known botnet IP ranges.

Comments are closed