Alert Level: 🚨 EXTREMELY HIGH RISK (Active Exploitation Confirmed)
Apple has confirmed that a critical new zero-day vulnerability, tracked as CVE-2025-14174, is being actively exploited in the wild to attack users. This is a serious threat affecting almost all Apple devices.
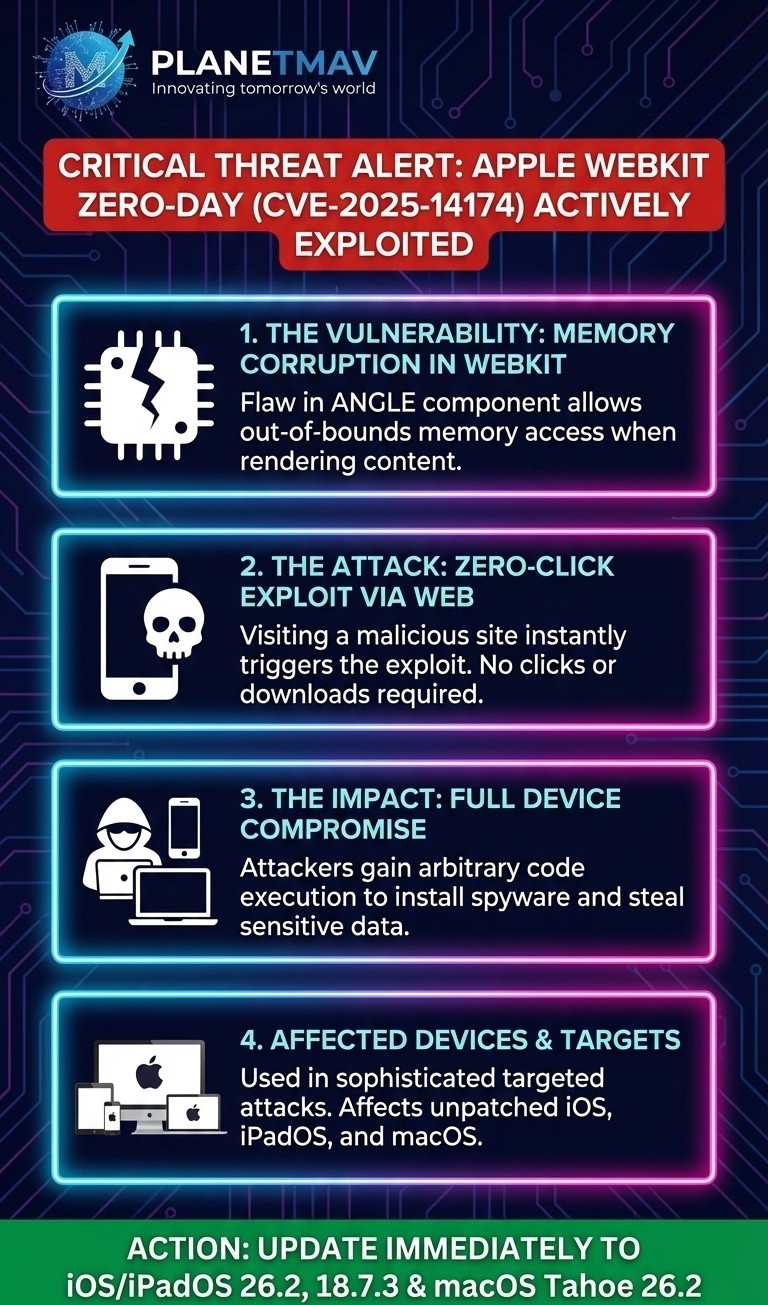
1. The Vulnerability Explained
This vulnerability is a memory corruption flaw within WebKit, the open-source browser engine that powers Safari and all web browsers on iOS and iPadOS (like Chrome and Firefox for iOS).
- The Flaw: Specifically, it is an “out-of-bounds memory access” issue within a component called ANGLE (Almost Native Graphics Layer Engine), which WebKit uses for rendering graphics.
- How it works: When a user visits a maliciously crafted website, the website’s code can trick WebKit into accessing memory locations outside of its allocated boundaries. This “out-of-bounds” access corrupts the device’s memory.
- The Result: This memory corruption can be weaponized by an attacker to execute arbitrary code on the device. In simpler terms, just visiting a bad webpage can allow a hacker to run their own malicious commands on your iPhone, iPad, or Mac, potentially installing spyware or stealing data.
2. The “Zero-Day” Nature & Active Exploitation
A “zero-day” means the vulnerability was unknown to Apple before it was discovered being used in attacks. There were “zero days” for Apple to fix it before hackers started exploiting it.
- Targeted Attacks: Apple has confirmed that this exploit is being used in “extremely sophisticated” attacks against specific individuals. This suggests it is likely being used by advanced threat actors, such as state-sponsored groups, to deploy mercenary spyware.
- No User Interaction Required: The most dangerous aspect of this flaw is that it requires no special action from the user other than visiting a webpage. The exploit is triggered automatically when the browser renders the malicious content.
3. Affected Products & Linking to Google Chrome
Because the flaw is in WebKit’s ANGLE component, which is a cross-platform graphics library also used by Google Chrome, this vulnerability affects a wide range of software.
- Apple Devices: All devices running older versions of iOS, iPadOS, macOS, tvOS, and watchOS are vulnerable.
- Google Chrome: Google also patched this same vulnerability in the desktop version of Chrome on December 10, 2025.
4. Immediate Action Required: UPDATE NOW
Apple has released emergency security updates to patch this vulnerability. Because it is being actively exploited, installing these updates immediately is critical.
Patched Versions:
- iOS & iPadOS: 26.2 and 18.7.3
- macOS: Tahoe 26.2, Sequoia 15.7.3, Sonoma 14.8.3
- Safari: 26.2
- tvOS & watchOS: 26.2
(Source:)
Go to Settings > General > Software Update on your mobile devices, or System Settings > General > Software Update on your Mac, and install the update now.

Comments are closed